Recording encryption key overview
Genesys Cloud uses encryption keys that are unique for each organization. These encryption keys protect recordings from unauthorized access to the following information:
- Call recordings
- Digital recordings (email, chat, message)
- Transcript of a corresponding recording when transcription is enabled
Genesys Cloud supports the following encryption key management methods:
- Genesys Cloud Managed Keys: Genesys Cloud generates and stores the public/private KEK key pairs that the recording encryption process uses. This method enables you to manage the KEKs that exist in Genesys Cloud; however, Genesys Cloud owns the keys. You do not need to maintain copies of the KEKs. You can access the recordings in decrypted form for playback, download, or bulk export.
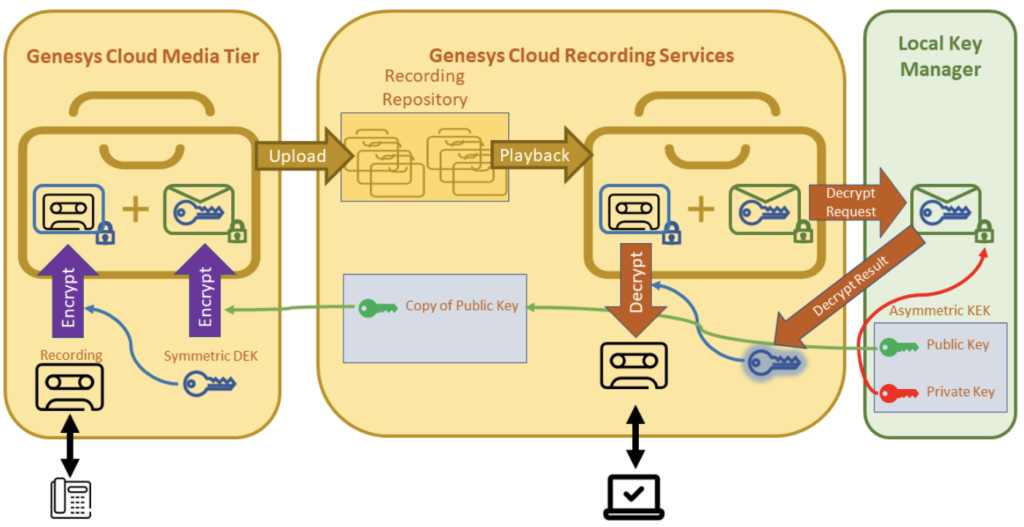
- Local key manager (LKM): Your organization implements a service to generate public/private KEK key pairs and stores them.
Click the image to enlarge.
When you work with LKM, Genesys Cloud uses the same envelope encryption technique for recording encryption and uses your public key as the KEK. To decrypt the recording, the encrypted DEK is first sent to LKM for decryption. The decrypted DEK then returns to Genesys Cloud and is used to decrypt the recording. The private KEK key never enters Genesys Cloud.
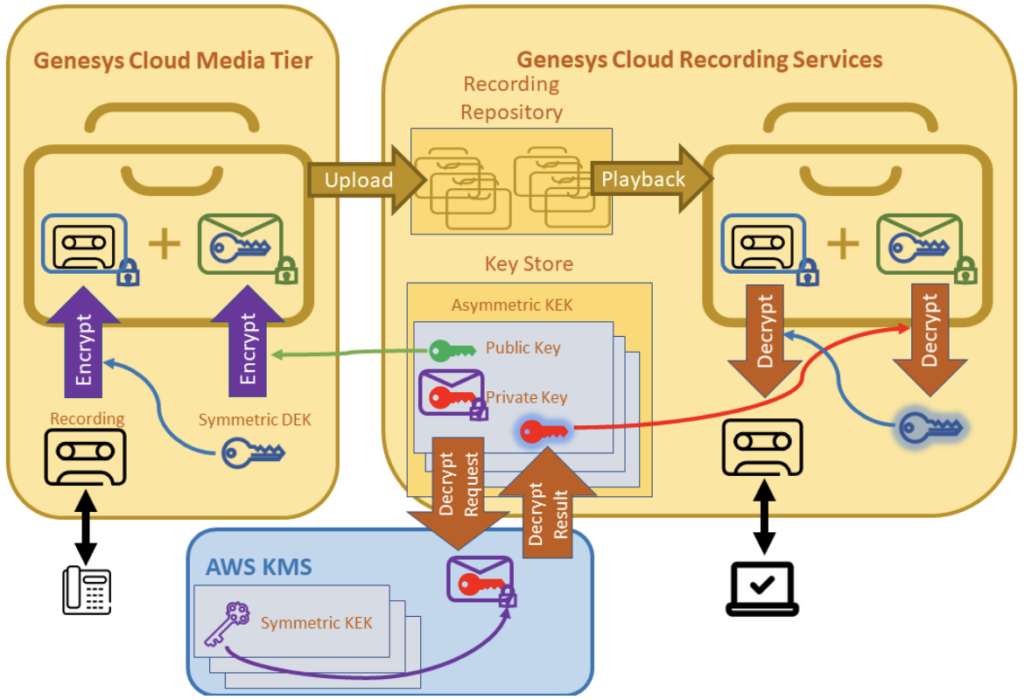
- AWS KMS symmetric: Your organization encrypts the private Genesys Cloud managed KEK key pairs with the symmetric keys that you receive from the AWS Key Management Service (KMS). Similar to LKM, this option allows you to assert access control over recordings in Genesys Cloud. Genesys Cloud can decrypt recordings only as long as you grant access to the symmetric keys in AWS KMS.
Click the image to enlarge.
When you work with AWS KMS, Genesys Cloud uses the same envelope encryption technique for recording encryption. For recording decryption, AWS KMS first decrypts the private KEK key pair. After decryption, Genesys Cloud uses it to decrypt the DEK and the DEK is then used to decrypt the recording. Your symmetric AWS KMS key never enters Genesys Cloud.
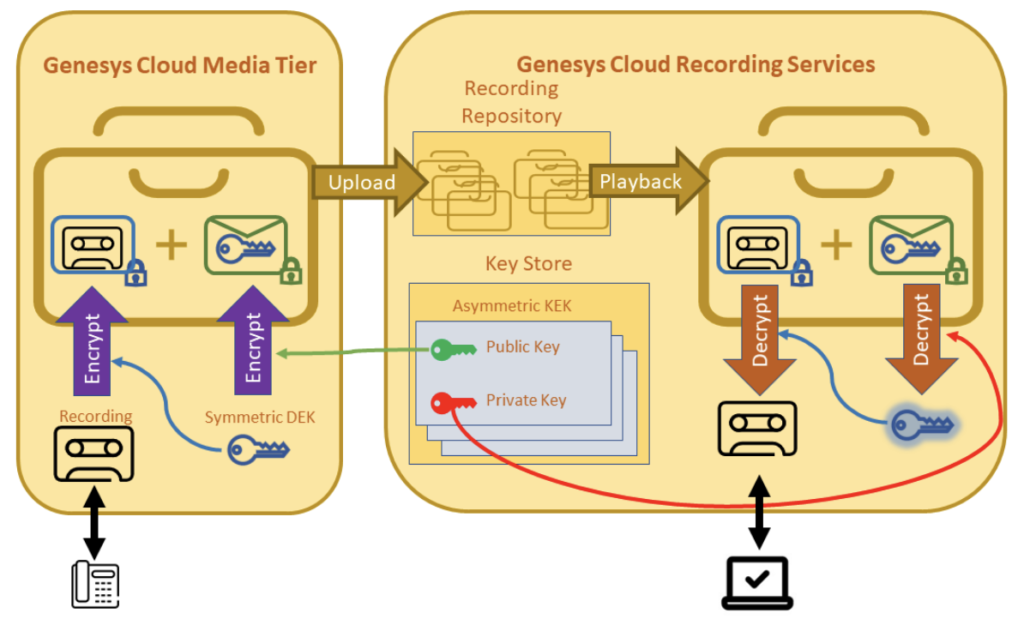
- For KEKs, Genesys Cloud creates RSA 3072-bit public/private key pairs. The public keys are published internally for encryption purposes. The private keys are used for decryption and never leave encryption services within Genesys Cloud. The public key and private key in a KEK key pair are mathematically linked.
- For DEKs, Genesys Cloud generates a different AES 256-bit symmetric key per recording.
- The DEKs are encrypted by the public keys associated with the KEK key pairs and can only be decrypted by corresponding private keys.
Genesys Cloud Media Tier abides to the above encryption process when the system creates and safely stores recordings. This process includes Media Tier’s intermediary storage before the encrypted files are uploaded to the recording repository. The Media Tier’s intermediary storage resides within Genesys Cloud with Genesys Cloud Voice or BYOC Cloud, or on premise with BYOC Premises. The use of long and strong cryptographic keys provides an effective defense against brute force attacks.
When you must decrypt recordings, for example, when responding to a user’s recording playback request, the following decryption process occurs after the file is retrieved from the recording repository:
- The encrypted DEK is decrypted using the corresponding private key associated with the KEK key pair.
- With DEK, the encrypted recording is decrypted.
The same decryption process occurs when you bulk export recordings. The exported recording files are no longer encrypted with the previously mentioned encryption keys. However, they are secured in the exported S3 bucket with server-side encryption (SSE) enabled as per your policy with Amazon S3 managed encryption keys (SSE-S3), or with Customer Managed Keys (CMKs) that AWS Key Management Service (SSE-KMS) stores. Also, you can specify a PGP-compatible encryption to encrypt the files as they are exported.
Click the image to enlarge.
Change encryption keys regularly to help ensure the safety of your recorded interactions. This procedure limits the number of recordings that a specified key can access.
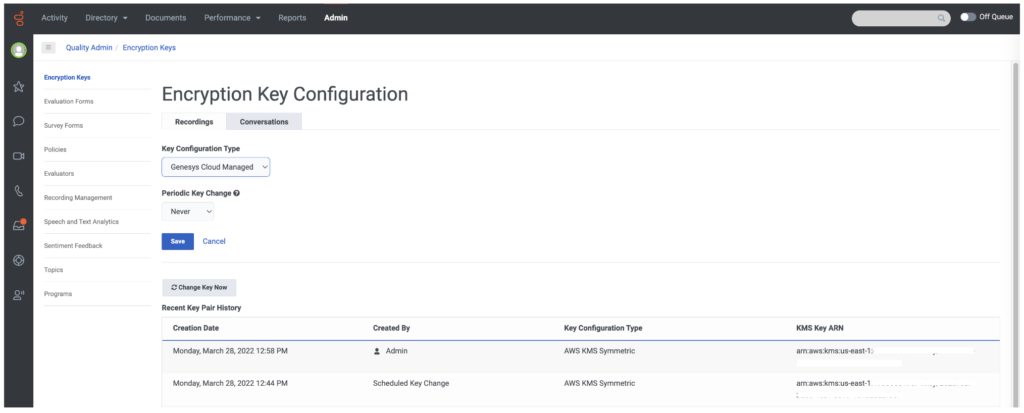
- With Genesys Cloud managed keys, you can change the KEKs in the Encryption Key UI. For more information, see Modify the key change schedule and Change encryption key now.
- With Local Key Manager, you must change keys that exist in your key service.
- With AWS KMS Symmetric, you can change the symmetric key in AWS KMS, and then change the KEKs in the Encryption Key UI. See the Rotate Keys in AWS KMS section in Use an AWS KMS symmetric key for recordings.