Local key management
By default, Genesys Cloud generates and stores the public/private key pair used by the recording encryption process. When working with local key management, your developers must write a service that generates the key pairs and stores them on premises. Genesys Cloud accesses your local key manager every time the private key is required. Your organization is responsible for implementing this service and storing keys safely. Local key management is useful when for compliance reasons you must manage your own keys.
- Genesys recommends that you only use local key management if you must do so for compliance reasons and you understand the implications of managing your own keys.
- When working with local key management, you possess the only copy of your private keys. If these keys are lost or destroyed, the recordings that are encrypted with the lost keys are permanently encrypted and therefore unusable. If you use local key management, ensure that you protect your private keys from theft or accidental destruction.
Setup local key management
To use local key management, create a key management service. Genesys Cloud uses this service to access your public keys. After you implement local key management, the service that you developed handles key management for you.
For more information about how to create your own key management service and an example code, see https://github.com/MyPurecloud/local-key-manager.
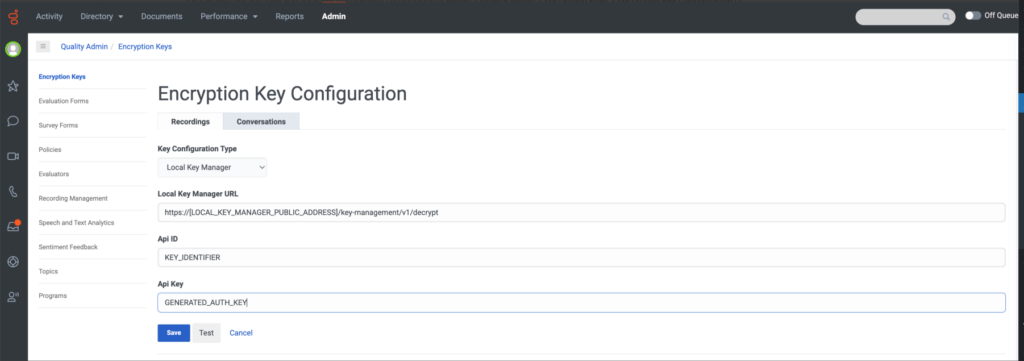
As shown below, you can also test and save your local key management configuration in Admin > Quality > Encryption Keys > Encryption Key Configuration.
Click the image to enlarge.