Use an AWS KMS symmetric key for recordings
To enable the use of AWS KMS as the recording keystore for Genesys Cloud, you must create keys in AWS KMS and set up the key configurations in Genesys Cloud. With this setup, the private keys in KEK key pairs will be encrypted by the symmetric key provided by your organization via KMS. This ensures your organization’s access control for recordings. Genesys Cloud requires the decryption of the private keys with the keys provided by your organization for recording decryption.
- Create a customer managed key in your AWS account. This key must be in the same core region as your Genesys Cloud home region. For multi-region keys, ensure that either the primary region or a replicated region matches your Genesys Cloud home region.
- Edit the key policy to grant access to Genesys Cloud, so that Genesys Cloud can access your KMS keys. Use 765628985471 (Core/Satellite regions) for the account ID. If required, please contact your Genesys representative for the FedRAMP region [US-East-2] account ID.
- Edit the key policy to include a condition that only allows requests initiated from your Genesys Cloud organizations.
The following is an example of the key policy.
{
“Sid”: “Allow use of the key”,
“Effect”: “Allow”,
“Principal”: {
“AWS”: [
“arn:aws:iam::765628985471:root”
]
},
“Action”: [
“kms:Encrypt”,
“kms:Decrypt”,
“kms:GenerateDataKey*”,
“kms:DescribeKey”
],
“Resource”: “*”,
“Condition”: {
“StringEquals”: {
“kms:EncryptionContext:genesys-cloud-organization-id”: [“orgId1”, “orgId2”, …]
}
}
}
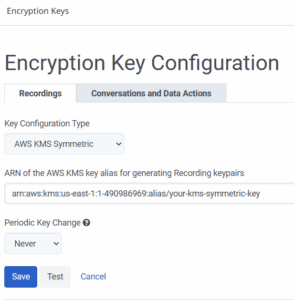
- Click Admin > Quality > Encryption Keys.
- Select the Recordings tab and click Edit.
- Click Menu > Conversation Intelligence > Recording and Policies > Encryption Keys.
- Click Edit.
- From the Key Configuration Type drop down list, select AWS KMS Symmetric.
- Enter the alias ARN associated with your KMS key in the ARN of the AWS KMS key alias for generating Recording keypairs text box.
The key alias ARN can be found in the AWS KMS console. It should look like “arn:aws:kms:{region}:{accountId}:alias/{your-alias}”. - From the Periodic Key Change list, select how often you want to generate new key pairs. Keys can be rotated daily, weekly, monthly, yearly, or never.
- Click the Test button to validate your configuration without saving it. The test will generate a data key pair from your specified KMS key, encrypt test data, decrypt it, and then assert that test data came out the same as it started. This helps to ensure that the configuration is safe to use.
- Click Save to save your configuration.
If your configuration is successfully saved, a new key pair is generated and displayed in the Recent Key Pair History list.
Error responses from KMS are displayed in the Encryption Key Configuration page to help diagnose the KMS issue.
Genesys Cloud will not be able to decrypt any recordings until KMS availability is restored.
You can rotate the AWS KMS keys that Genesys Cloud is using. You can choose to use either manual or automatic KMS rotation mechanisms.
- Manual rotation: Create a new KMS key, give it the same key policy, and then update the alias in KMS to point at the new key.
For more information, see: How can I manually rotate customer managed keys in AWS KMS? - Automatic rotation: Occurs transparently. For more information, see: Rotating AWS KMS keys.

