Manage Genesys Cloud embedding
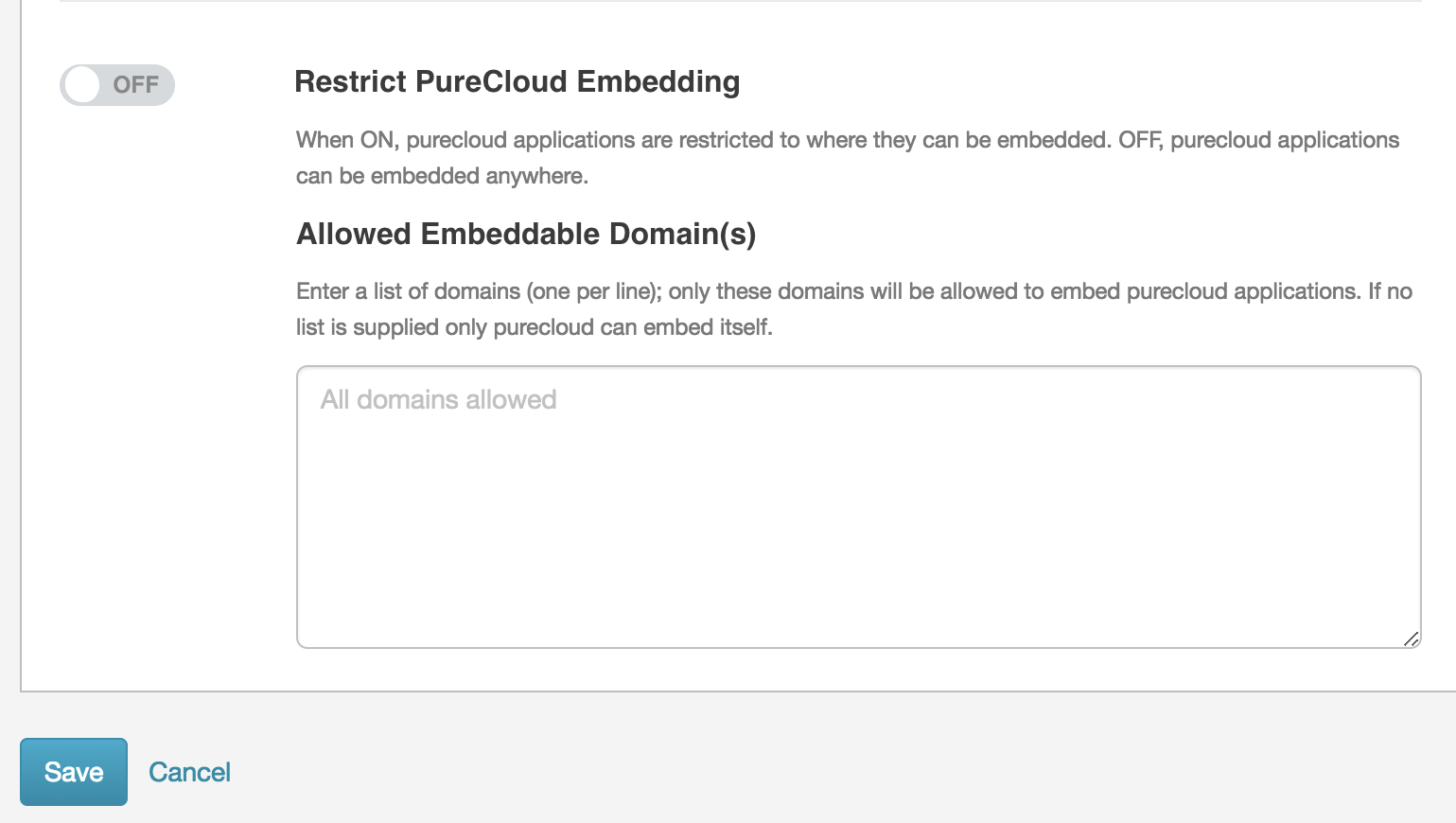
Restrict Genesys Cloud Embedding is an optional security setting that prevents external websites from embedding an instance of your Genesys Cloud org in an iframe. It combats “clickjacking,” a malicious technique that redirects a user to a website under the attacker’s control. The malicious website impersonates the victim’s website by embedding it within an iframe element.
Warning: Enabling this feature makes unusable any Genesys Cloud application or integration that embeds Genesys Cloud into an iframe, whose domain does not appear in Allowed Embeddable Domain(s) box.
Configure Genesys Cloud to allow iframes for the legitimate domains with which your organization works. If you do not add these domains, integrations such as Genesys Cloud for Salesforce, Genesys Cloud for Zendesk, Genesys Cloud for Chrome, Genesys Cloud for Firefox, and Genesys Cloud Embeddable Framework will not work. For more information, see Manage Genesys Cloud embedding with the Genesys Cloud embedded clients.
Using deceptively crafted style sheets, iframes, and text boxes, clickjacking makes users think they are interacting with the genuine web application, when they are actually interacting with an invisible iframe controlled by an attacker.
The malicious site monitors actions performed by the user, and may use transparent or opaque layers to trick a user into clicking a button or link that appears to be legitimate. By “hijacking” user clicks, an attacker can route the user to a different page, application, or domain. Keystrokes can be hijacked using similar techniques. A clickjacking victim can inadvertently pass credentials or other information to an attacker.
To restrict Genesys Cloud embedding:
By default, Restrict Genesys Cloud Embedding setting is not enabled in your Genesys Cloud organization. Before enabling the Restrict Genesys Cloud Embedding setting, add any domains who can legitimately iframe your Genesys Cloud org in the Allowed Embeddable Domain(s) box. If you do not add these domains, then integrations and embedded clients do not work.
- Click Admin.
- Under Account Settings, click Organization Settings.
- Click Menu > Account > Organization Settings.
- Click the Settings tab.
- Scroll to the Security & Compliance section.
-
In the Allowed Embeddable Domain(s) box, add the name of any domains that legitimately iframe your Genesys Cloud org. The table below lists domains that each Genesys Cloud embedded client must be able to access. Use wildcards to include subdomains. Enter each domain entry on its own line. You can add up to 10 domain entries to this list.
Genesys Cloud embedded client Domain Genesys Cloud Embeddable Framework Parent domain Genesys Cloud for Chrome chrome-extension://onbcflemjnkemjpjcpkkpcnephnpjkcb Genesys Cloud for Firefox moz-extension://* Genesys Cloud for Salesforce *.salesforce.com
*.force.com
Genesys Cloud for Zendesk *.zendesk.com
*.zdusercontent.com
Genesys Cloud for Microsoft Teams *.teams.microsoft.com
*.skype.com
-
Enable the Restrict Genesys Cloud Embedding setting and add domains. The system displays a warning to remind that this feature, when enabled, could make integrations and apps unusable if the list of allowed domains is empty or invalid.
Warning: Enabling this feature could cause Genesys Cloud integrations, Genesys Cloud apps, and any other application or integration that uses an iframe to load in Genesys Cloud, whose domain is not listed in Allowed Embeddable Domain(s), to be unusable. -
Click Save.
Important: When you enable or disable Restrict Genesys Cloud Embedding, users must log out and log back in to their embedded clients.
Technical Notes
When Restrict Genesys Cloud Embedding is on, Genesys Cloud uses the Content Security Policy (CSP) frame-ancestors directive to restrict which domains can embed an instance of Genesys Cloud using <frame>, <iframe>, <object>, <embed>, or <applet> elements. For a list of compatible browsers, see CSP:frame-ancestors at Mozilla Developer Network web documentation.
When the feature is turned on, users must log out and log in, to obtain a new cookie that applies security headers to HTML requests. When the feature is turned off, the Auth API will delete their cookie at the next login.

