Genesys Cloud
2024 Genesys CIDR expansion and firewall requirements notification – commercial
| Announced on | Effective date | Aha! idea |
|---|---|---|
| 2024-05-27 | 2025-05-03 | - |
Description
Genesys purchased an additional /18 CIDR block of IP addresses for Genesys Cloud public-facing media services. These addresses supplement existing regions and cover growth in future regions. This announcement serves notice that customers must configure their firewalls to allow access to the new CIDR IP addresses now. This action ensures that the organization is ready for the cutover to the new CIDR ranges on the effective date.
- The new range is (136.245.64.0/18)
- On the effective date, Genesys Cloud’s media services will also fully migrate Africa (Cape Town), and Asia Pacific (Jakarta) to the Genesys-owned CIDR addresses. Genesys Cloud’s cloud media services will be fully migrated to Genesys-owned CIDR ranges in all supported regions. For more information, see Cloud media services CIDR IP address range.
- On the effective date, Genesys Cloud will also expand the Media RTP port range from udp/16384-32768 to udp/16384-65535.
- Genesys will also move all Force TURN services from its current static IP address to Genesys owned CIDR addresses.
Watch the video
In addition to the content in this article, Genesys has prepared the accompanying video that describes the CIDR expansion updates and the steps you need to perform if you’re impacted by the change. While this video provides a nice introduction to the CIDR expansion and shows examples of the tests, Genesys recommends that you read the entire article. Do not rely solely on the video.
What does this mean?
- Genesys Cloud will expand the range of Genesys-owned IP addresses for use in media services.
- In addition to the new address range, Genesys will move the Jakarta, and Cape Town regions from AWS-owned IPs to the Genesys ranges. Affected customers must allow connections to the new range (136.245.64.0/18), in addition to the existing Genesys CIDR ranges.
- Genesys is expanding the Media RTP port range from udp/16384-32768 to udp/16384-65535. Customers must ensure outbound connections are allowed to the expanded RTP range as well as the corresponding ingress response traffic.
- Genesys cloud Force TURN services will move from Amazon-owned IP addresses to Genesys Cloud-owned CIDR IP addresses.
Am I affected?
The following customers are affected:
- Customers who use firewall policies to restrict outbound connections from Genesys Cloud clients, phones, and Edge devices are affected. Network administrators can view detailed information about affected services, addresses, and ports, and perform the self-readiness checks. For more information, see Cloud media services CIDR IP address range.
- Customers who operate organizations based out of Africa (Cape Town), Asia Pacific (Jakarta), or any customers who use these regions via Global Media Fabric and use firewall policies to restrict outbound connections from Genesys Cloud clients, phones, and Edge devices will be affected.
- Customers who use Genesys Cloud for voice interactions, video, and screen recordings are affected.
- Customers using firewall policies to restrict outbound connections from Genesys Cloud WebRTC clients that have Force TURN enabled are affected.
What do I need to do to prepare for this expansion?
If any of the items mentioned in the A, B, C, or D bullet points in any of the sections above apply to your Genesys Cloud organization, then you need to take these steps to prepare for the Genesys CIDR expansion.
- Update your firewall allowlist by adding the new CIDR block of IP addresses (136.245.64.0/18) to the existing list of previously announced Genesys CIDR blocks.
- Ensure outbound connections are allowed to the full RTP port range (16384-65535) as well as the corresponding ingress response traffic.
- All Force TURN documentation is based on IP address. In the event that you are doing any advanced filtering based on DNS name, note that the Force Turn IPs now resolve
turn.x.x.xand notturn-premium.x.x.x.
The following sections contains tests that allow you to confirm your organization's readiness for the new CIDR IP address range and the RTP port expansion. Genesys recommends that you run the tests for each Genesys Cloud feature that your organization uses.
If you use WebRTC phones in your organization, the tests in this section allow you to confirm WebRTC client readiness for the CIDR IP address range and RTP port expansion. You need to run these tests on the same networks in which your Agent WebRTC clients operate.
The WebRTC Diagnostics App – Network Test is a very basic test that verifies DNS resolution and general connectivity to STUN/TURN services.
- You must log in to Genesys Cloud to run the WebRTC Diagnostics app.
- When testing CIDR, you only need to run the Network Test.
- If you have recently used your phone, you'll need to disconnect the persistent connection before you run the diagnostic. For more information, see Terminate a persistent connection on a Genesys Cloud WebRTC phone.
- Access the Genesys Cloud WebRTC Diagnostics app for your region:
- Select Network Test.
Network Test
The Network Test verifies that your network can access the Genesys media servers. More specifically, these tests confirm that DNS resolution is working and that you are able to connect to the public AWS pool and to the new Genesys Cloud cloud media services CIDR IP range.
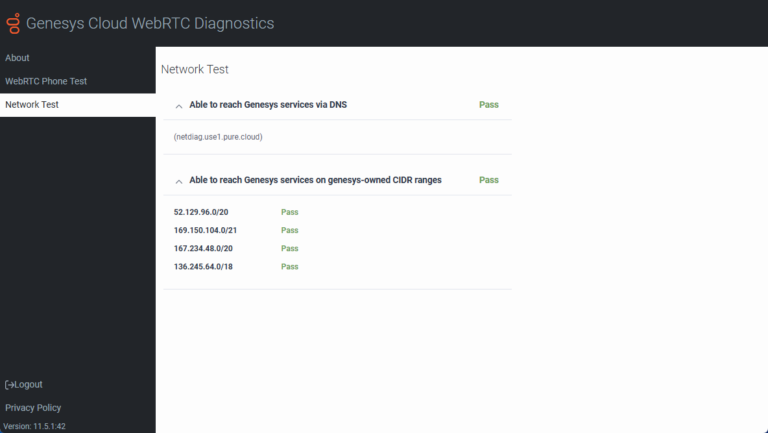
If you encounter errors when running the test, check your firewall settings against the recommended settings found in the About ports and services for your firewall article. If you still have problems, contact Product Support.
The advanced command line tests are designed for network professionals. These tests verify DNS resolution, STUN/TURN, and RTP port range. (The tcp/3478, udp/3478, and udp/16384-65535 destination transport protocols/ports.)
To ensure that the entirety of the address range is covered, you must run these tests against each one of the following destination FQDNs shown in this table - regardless of your home region.
| Americas | EMEA | Asia Pacific |
|---|---|---|
|
|
|
The following tables provide you with a set of cloud platform network connectivity diagnostic endpoints that you can use to test against. To perform the manual tests, you can use commonly available network connectivity tools, such as netcat and nmap.
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| tcp/3478 |
|
No specific response is displayed, but a successful connection handshake is indicated. | The connection times out. |
| udp/3478 | nmap -sU -p 3478 --script stun-info netdiag.use1.pure.cloud(You must be using nmap version 7.9 or later to run this command.) |
The response includes a stun-info section listing an external IP address. This response will include the following: nmap done: 1 IP address (1 host up) scanned in #.## seconds |
You receive a "host is down" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| udp/16384-65535 |
Repeat this command, replacing 16384 with a variety of ports from the bottom to the top of the new range. Examples:
|
The response includes: GoodbyeGoodbyeGoodbyeGoodbyeGoodbye (This command sends five packets, which result in five "Goodbye" responses; one for each packet.) |
You do not receive a "Goodbye" response. |
Use the following table as a reference for the Genesys CIDR traffic profile for WebRTC clients.
|
Services |
Source |
Destination address |
Destination transport protocol/port |
Description |
|---|---|---|---|---|
| STUN | WebRTC Client |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
tcp/3478 udp/3478 |
Identifies the public IP address of the WebRTC Client. |
| Media | WebRTC Client |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
udp/16384-65535 | Media sent to Genesys Cloud TURN or media services. |
If you use hardware phones in your organization, these tests allow you to confirm hardware phone readiness for the CIDR IP address range and RTP port expansion. You need to run these tests on the same networks in which the hardware phones operate.
The advanced command line tests are designed for network professionals. These tests verify DNS resolution, signaling, and RTP port range. (The tcp/8061, tcp/5061, and udp/16384-65535 destination transport protocols/ports.)
To ensure that the entirety of the address range is covered, you must run these tests against each one of the following destination FQDNs shown in this table - regardless of your home region.
| Americas | EMEA | Asia Pacific |
|---|---|---|
|
|
|
The following tables provide you with a set of cloud platform network connectivity diagnostic endpoints that you can use to test against. To perform the manual tests, you can use commonly available network connectivity tools, such as netcat and nmap.
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
|
tcp/8061
|
|
The response includes: Goodbye |
You do not receive a "Goodbye" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
|
tcp/5061 |
|
The response includes: Goodbye |
You do not receive a "Goodbye" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| udp/16384-65535 |
Repeat this command, replacing 16384 with a variety of ports from the bottom to the top of the new range. Examples:
|
The response includes: GoodbyeGoodbyeGoodbyeGoodbyeGoodbye (This command sends five packets, which result in five "Goodbye" responses; one for each packet.) |
You do not receive a "Goodbye" response. |
Use the following table as a reference for the Genesys CIDR traffic profile for hardware phones.
|
Services |
Source |
Destination address |
Destination transport protocol/port |
Description |
|---|---|---|---|---|
| Signaling | Hardware Phone |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
tcp/8061 tcp/5061 |
SIP signaling between the hardware phone and cloud platform SIP services. |
| Media | Hardware Phone |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
udp/16384-65535 | Media sent to Genesys Cloud media services. |
If you use BYOC Cloud for your telephony connection, these tests allow you to confirm BYOC Cloud's readiness for the CIDR IP address range and RTP port expansion. You need to run these tests on the same networks where the remote end of the BYOC Cloud trunk is terminated. (For example, SBC's or PBX’s network.)
The advanced command line tests are designed for network professionals. These tests verify RTP port range. (The udp/16384-65535 destination transport protocols/ports.) SIP is not included in this set of tests as the BYOC Cloud SIP Proxies do not run on the Genesys CIDR address range.
To ensure that the entirety of the address range is covered, you must run these tests against each one of the following destination FQDNs shown in this table - regardless of your home region.
| Americas | EMEA | Asia Pacific |
|---|---|---|
|
|
|
The following table provides you with a set of cloud platform network connectivity diagnostic endpoints that you can use to test against. To perform the manual tests, you can use commonly available network connectivity tools, such as netcat and nmap.
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| udp/16384-65535 |
Repeat this command, replacing 16384 with a variety of ports from the bottom to the top of the new range. Examples:
|
The response includes: GoodbyeGoodbyeGoodbyeGoodbyeGoodbye (This command sends five packets, which result in five "Goodbye" responses; one for each packet.) |
You do not receive a "Goodbye" response. |
Use the following table as a reference for the Genesys CIDR traffic profile for BYOC Cloud.
|
Services |
Source |
Destination address |
Destination transport protocol/port |
Description |
|---|---|---|---|---|
| Media | Customer’s Carrier or PBX Device |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
udp/16384-65535 | Media sent to Genesys Cloud media services. |
If you use ACD Screen Recording and Video Chat in your organization, these tests allow you to confirm these feature's readiness for the CIDR IP address range and RTP port expansion. You need to run these tests on the same networks on which ACD Screen Recording and Video Chat clients are being used.
The WebRTC Diagnostics App – Network Test is a very basic test that verifies DNS resolution and general connectivity to STUN/TURN services.
The Genesys Cloud WebRTC Diagnostics app provides you with a set of diagnostics that verifies your WebRTC configuration is properly configured and identifies potential problems.
- You must log in to Genesys Cloud to run the WebRTC Diagnostics app.
- When testing CIDR, you only need to run the Network Test.
- If you have recently used your phone, you'll need to disconnect the persistent connection before you run the diagnostic. For more information, see Terminate a persistent connection on a Genesys Cloud WebRTC phone.
- Access the Genesys Cloud WebRTC Diagnostics app for your region:

- Select Network Test.
Network Test
The Network Test verifies that your network can access the Genesys media servers. More specifically, these tests confirm that DNS resolution is working and that you are able to connect to the public AWS pool and to the new Genesys Cloud cloud media services CIDR IP range.

If you encounter errors when running the test, check your firewall settings against the recommended settings found in the About ports and services for your firewall article. If you still have problems, contact Product Support.
The advanced command line tests are designed for network professionals. These tests verify DNS resolution, STUN/TURN, and RTP port range. (The tcp/3478, udp/3478, and udp/16384-65535 destination transport protocols/ports.)
To ensure that the entirety of the address range is covered, you must run these tests against each one of the following destination FQDNs shown in this table - regardless of your home region.
| Americas | EMEA | Asia Pacific |
|---|---|---|
|
|
|
The following tables provide you with a set of cloud platform network connectivity diagnostic endpoints that you can use to test against. To perform the manual tests, you can use commonly available network connectivity tools, such as netcat and nmap.
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| tcp/3478 |
|
No specific response is displayed, but a successful connection handshake is indicated. | The connection times out. |
| udp/3478 | nmap -sU -p 3478 --script stun-info netdiag.use1.pure.cloud(You must be using nmap version 7.9 or later to run this command.) |
The response includes a stun-info section listing an external IP address. This response will include the following: nmap done: 1 IP address (1 host up) scanned in #.## seconds |
You receive a "host is down" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| udp/16384-65535 |
Repeat this command, replacing 16384 with a variety of ports from the bottom to the top of the new range. Examples:
|
The response includes: GoodbyeGoodbyeGoodbyeGoodbyeGoodbye (This command sends five packets, which result in five "Goodbye" responses; one for each packet.) |
You do not receive a "Goodbye" response. |
Use the following table as a reference for the Genesys CIDR traffic profile for ACD Screen Recording and Video Chat.
|
Services |
Source |
Destination address |
Destination transport protocol/port |
Description |
|---|---|---|---|---|
| STUN | Genesys Cloud Client |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
tcp/3478 udp/3478 |
Identifies the public IP address of the Screen Recording and Video Chat Client. |
| Media | Genesys Cloud Client |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
udp/16384-65535 | Media sent to Genesys Cloud TURN or media services. |
If you use BYOC Premises for your telephony connection, these tests allow you to confirm the BYOC Premises Edge appliance's readiness for the CIDR IP address range and RTP port expansion. You need to run these tests on the same networks on which the Edge appliances are connected.
The advanced command line tests are designed for network professionals. These tests verify WebRTC and hybrid media site link capability for BYOC Premises Edge. (The tcp/5061, tcp/3478, udp/3478, and udp/16384-65535 destination transport protocols/ports.)
To ensure that the entirety of the address range is covered, you must run these tests against each one of the following destination FQDNs shown in this table - regardless of your home region.
| Americas | EMEA | Asia Pacific |
|---|---|---|
|
|
|
The following tables provide you with a set of cloud platform network connectivity diagnostic endpoints that you can use to test against. To perform the manual tests, you can use commonly available network connectivity tools, such as netcat and nmap.
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
|
tcp/5061 |
|
The response includes: Goodbye |
You do not receive a "Goodbye" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| tcp/3478 |
|
No specific response is displayed, but a successful connection handshake is indicated. | The connection times out. |
| udp/3478 | nmap -sU -p 3478 --script stun-info netdiag.use1.pure.cloud(You must be using nmap version 7.9 or later to run this command.) |
The response includes a stun-info section listing an external IP address. This response will include the following: nmap done: 1 IP address (1 host up) scanned in #.## seconds |
You receive a "host is down" response. |
| Destination protocol / port | Sample test command | Successful response | Failed response |
|---|---|---|---|
| udp/16384-65535 |
Repeat this command, replacing 16384 with a variety of ports from the bottom to the top of the new range. Examples:
|
The response includes: GoodbyeGoodbyeGoodbyeGoodbyeGoodbye (This command sends five packets, which result in five "Goodbye" responses; one for each packet.) |
You do not receive a "Goodbye" response. |
Use the following table as a reference for the Genesys CIDR traffic profile for BYOC Premises Edge appliances.
|
Services |
Source |
Destination address |
Destination transport protocol/port |
Description |
|---|---|---|---|---|
| WebRTC Signaling | BYOC Premises Edge Appliance |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
tcp/5061 | Control plane signaling between the Edge device and cloud XMPP Gateway. |
| WebRTC TURN | BYOC Premises Edge Appliance |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
udp/16384-65535 | Media sent to Genesys Cloud TURN services. |
| WebRTC STUN | BYOC Premises Edge Appliance |
52.129.96.0/20 169.150.104.0/21 167.234.48.0/20 136.245.64.0/18 |
tcp/3478 udp/3478 |
Used to identify a public IP address of the Edge device. |
What if I need help or have questions?
Contact your Genesys Technical Account Manager or your Customer Success Manager. You can also contact My Support.

