Use an AWS KMS symmetric key for conversations
Symmetric keys managed in AWS KMS can be configured to encrypt and decrypt customer secured conversation data. Genesys Cloud generates data keys from your symmetric key in KMS. Customer secured conversation data is encrypted with these data keys. To decrypt conversation data, Genesys Cloud makes a request to KMS to decrypt the relevant data key. After the request is authorized, the data is decrypted.
- Create a customer managed key in your AWS account.
- Set the key type to Symmetric.
- Set the key usage to Encrypt and decrypt.
- Edit the key policy to grant access to Genesys Cloud, so Genesys Cloud can access your KMS keys. Use 765628985471 (Core/Satellite regions) for the account ID. If needed, please contact your Genesys representative for the FedRAMP region [US-East-2] account ID.
- Edit the key policy to include a statement to only allow requests that initiate from your Genesys Cloud organizations.
The following is an example of the key policy statement:
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::765628985471:root"
]
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:EncryptionContext:genesys-cloud-organization-id": ["orgId1", "orgId2", ...]
}
}
}
- Click Admin > Quality > Encryption Keys.
- Click Menu > Conversation Intelligence > Recording Policies > Encryption Keys.
- Select the Conversations tab and click Edit.
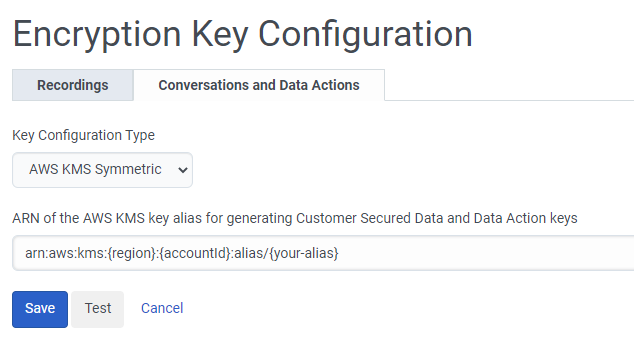
- From the Key Configuration Type list, select AWS KMS Symmetric.
- Enter the alias ARN associated with your KMS key in the ARN of the AWS KMS key alias for generating Customer Secured Data key text box.
The key alias ARN can be found in the AWS KMS console. It should look like “arn:aws:kms:{region}:{accountId}:alias/{your-alias}”. - Click the Test button to validate your configuration without saving it. The test generates a data key pair from your specified KMS key, encrypts the test data, decrypts it, and then asserts that test data came out the same as it started. This test helps to ensure that the configuration is safe to use.
- Click Save to save your configuration.
Click the image to enlarge.
This action removes your encryption key configuration for conversations.