Configure Google Cloud Platform
Special configurations for Google Cloud Functions (1st gen)
To use Google Cloud Functions (1st gen), you must configure functions, roles, and permissions in the Google Cloud Platform.
The following table lists the names of items used in the examples and describes their relationship to each other.
| Google item | Name in example | Description | Notes |
|---|---|---|---|
| Project | BusinessCallingAPI | This project contains the service account and functions. | |
| Service Account | jwt-testing |
This service account belongs to the BusinessCallingAPI project. |
|
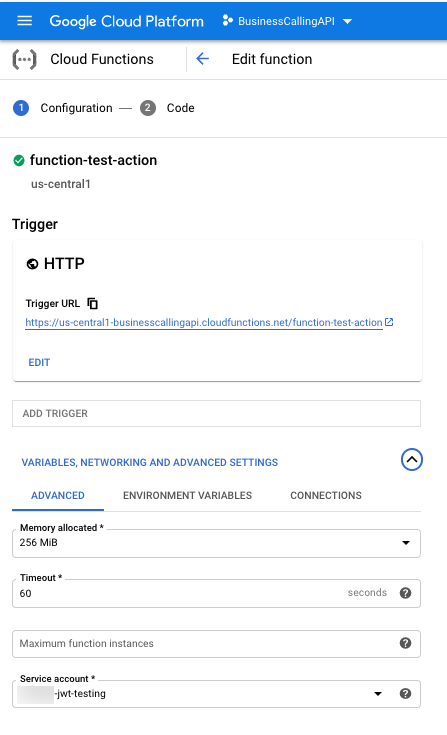
| Function | function-test-action | This function exists in the project BusinessCallingAPI. The service account jwt-testing is assigned to this function. | Assign the service account to each function that you want the Google data actions integration to execute. |
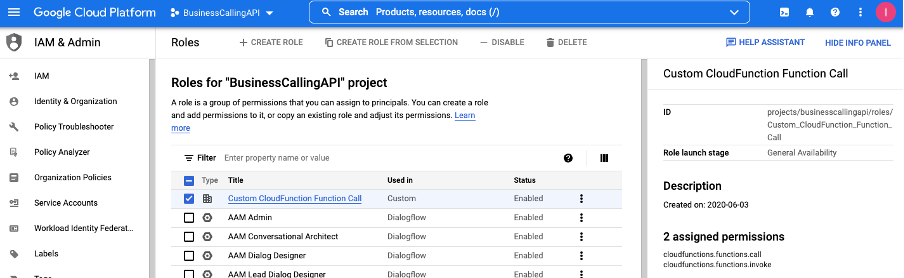
| Custom role | Custom CloudFunction Function Call | This custom role with the permissions cloudfunctions.functions.call and cloudfunctions.function.invoke is assigned to the function function-test-action for the service account jwt-testing. | Assign the custom role to the service account for each function that you want the Google data actions integration to execute. |
| Permission |
cloudfunctions.functions.call cloudfunctions.function.invoke |
These permissions are added to the custom role Custom CloudFunction Function Call. |
To use the Google data actions integration, configure your Google Cloud Platform account to link Google APIs to the integration.
- Create a service account.
This service account must be in a Google Cloud Platform project that contains APIs that you want data actions to call. For more information, see Creating and managing service accounts in the Google Cloud documentation.
If you want to use multiple APIs, make sure that the service account contains all the APIs that you want to use. If the APIs that you want to use span service accounts, then add a separate integration for each service account. For more information, see Add a data actions integration.
- Create a private key file for the service account.
This file contains details that you must add to the integration credentials. For more information, see Creating and managing service account keys in the Google Cloud documentation.
- Create or review existing Google Cloud Functions (1st gen).
- Make sure that the functions return JSON as their responses.
- Gather the project name, function locations, and function names.
Use this information to create the Request URL Template for the data action, which calls the function. For more information, see Add configuration to custom actions for integrations.
For a working example, see Example Google Cloud Function with a data action.
- Create a custom role and assign the cloudfunctions.functions.call and cloudfunctions.function.invoke permissions to the role.
The role now has permission to access functions and use the trigger endpoint for the function. For more information, see Understanding IAM custom roles in the Google Cloud documentation.
The following image shows the custom role Custom CloudFunction Function Call with the assigned permissions.
-
Assign the service account to each function that you want the data actions integration to execute. For more information, see Function Identity in the Google Cloud documentation.
The following image shows a list of functions. The function function-test-action is assigned the role Custom CloudFunction Function Call that exists in the service account jwt-testing.
Click image to enlarge.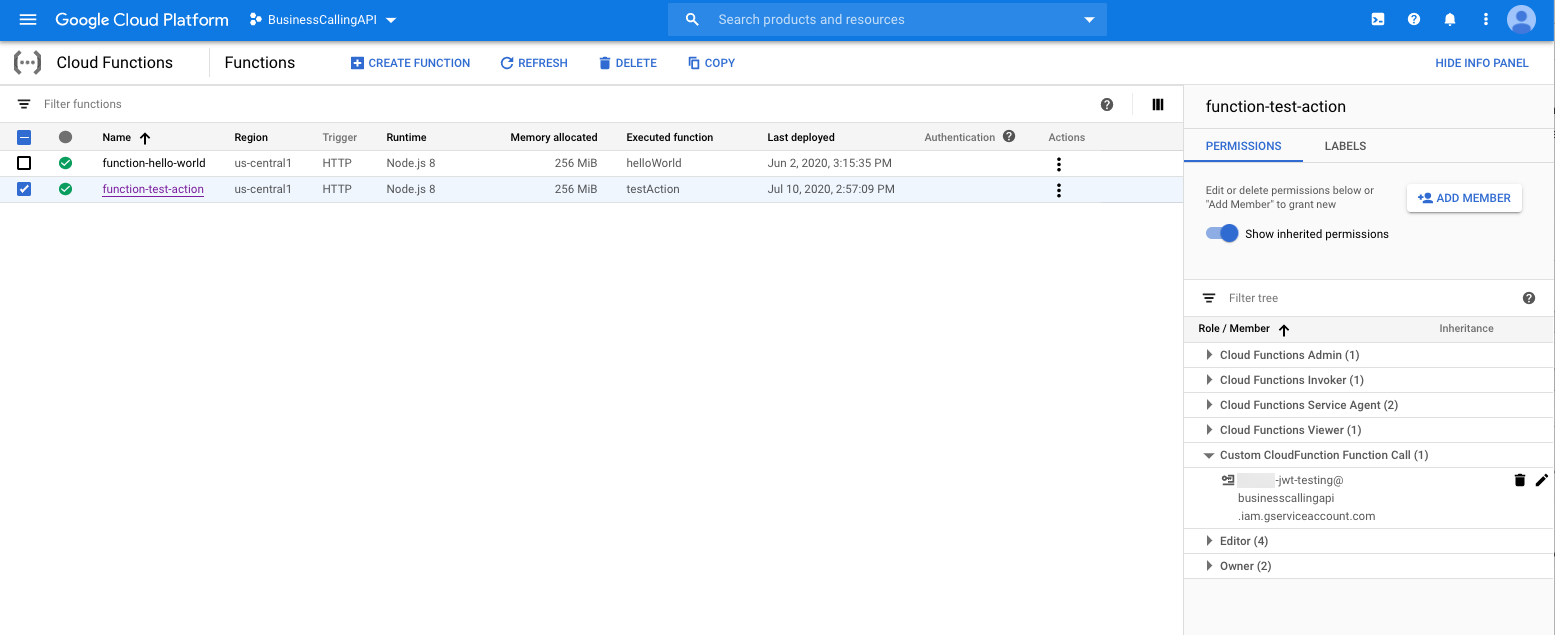
Use the trigger endpoint with functions
The following image shows the details about the function function-test-action. The service account jwt-testing is assigned to the function. Use the trigger endpoint to execute functions.
You are now ready to add a Google data actions integration to your Genesys Cloud organization.
Next, add the integration.
For more information, see About the Google data actions integration.