Create IAM resources to invoke an AWS Lambda function
To access AWS Lambda functions, Genesys Cloud must have permission to use resources in your Amazon Web Services (AWS) account. This procedure explains how to create a policy, create an IAM role in AWS, and attach this role to the policy. Later you assign this role to the AWS Lambda data actions integration in Genesys Cloud.
To create a policy, create an IAM role, and attach this role to the policy, follow these steps:
- Log in to AWS.
- Navigate to the AWS Services page.
- Retrieve the ARN on the AWS Lambda function that you want Genesys Cloud to invoke.
- Click Lambda.
- Select the AWS Lambda function that you want to invoke.Note: The AWS Lambda integration supports cross-region invocations. Administrators can invoke Lambdas that exist in a different AWS region from their Genesys Cloud organization as data actions. For more information, see AWS regions for Genesys Cloud.
- Copy the ARN for the AWS Lambda function. You use this ARN on a policy that you create.
- Click IAM.
- Create a policy. Policies specify what resources roles can act on and how roles can act on the resources.
- Under Dashboard, select Policies.
- Click Create policy.
- On the Visual editor tab, configure the following items:
- Under Service, click Choose a service and click Lambda. This setting specifies what service the policy calls.
- Under Actions and Access level, click the arrow next to Write and select the invokeFunction check box. This setting specifies what actions the policy grants to the AWS Lambda function.
- Under Resources, select Specific and click Add ARN. Paste the ARN that you copied from the AWS Lambda function in step 3. This setting specifies to which AWS Lambda function the policy grants the invoke permission.
- Click Review policy.
- In the Name box, type a name for the policy.
- Click Create policy.
- Create a role that uses this policy.
- Under Dashboard, click Roles.
- On the Roles page, click Create role.
- Select Another AWS Account as the type of trusted entity.
- In the Account ID box, enter 765628985471 (Core/Satellite regions) or 325654371633 (FedRAMP region (US-East-2)). This number is Genesys Cloud’s production AWS account ID.
- Select the Require external ID check box and enter your Genesys Cloud organization ID.
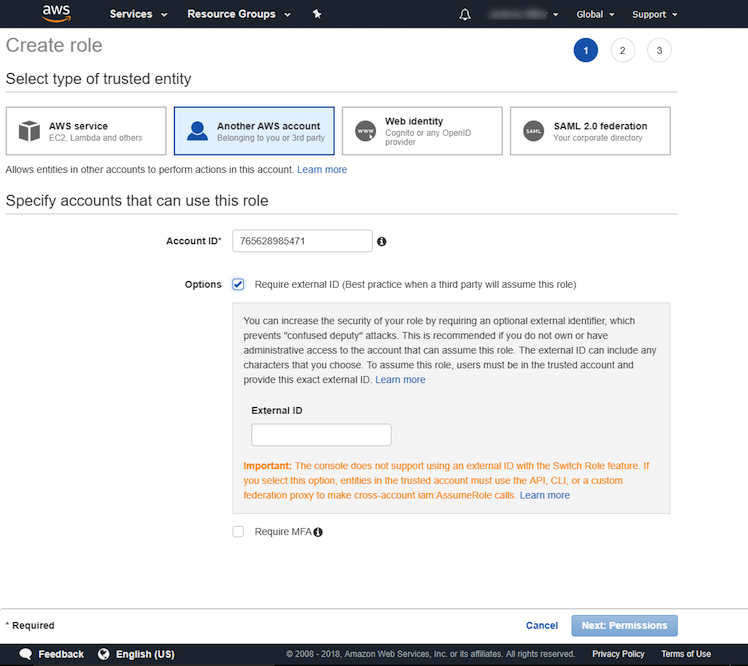
- Click Next: Permissions.
- Attach permission policies to this role.
- Select the policy that you created.
- Click Next: Review.
- In the Role name box, type a name for the role.
- In the Role description box, enter descriptive text about the role.
- Verify that the account number for Trusted entities matches the Genesys Cloud production AWS account ID that you entered earlier.
- Click Create role.
- Click the name of the role that you created. Summary details about the role appear.
- If you want more than one Genesys Cloud organization to be able to invoke the AWS Lambda function, then add multiple Genesys Cloud organization IDs to the JSON.
- Click Trust relationships.
- Click Edit trust relationship.
- Under sts:ExternalId, add additional Genesys Cloud organization IDs. See the following example.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::765628985471:root" }, "Action": "sts:AssumeRole", "Condition": { "StringLike": { "sts:ExternalId": [ "91cf9239-f549-465b-8cad-9b46f1420818", "90b7f8c9-790e-43f9-ad67-92b61365a4d0" ] } } } ] } - Click Update Trust Policy.
- Copy the Role ARN by clicking the Copy icon to the right of Role ARN. You use this Role ARN for your credentials when you add an AWS Lambda data action integration in Genesys Cloud.
Next, add an AWS Lambda data actions integration.
For more information about the integration, see About the AWS Lambda data actions integration.

